Saurik really is a jack of all trades. Not only is he the mastermind behind Cydia, essentially a 3rd party App Store for Jailbroken iOS devices, but he is also behind numerous Cydia tweaks and iOS frameworks. To top all of this off Saurik even turned his attention to Android back in May when he released both Cydia Substrate and Winterboard for Android.
It looks like Saurik isn’t done with Android just yet though…
He has tweeted today that he has just patched a severe security vulnerability that plagues 99% of Android devices that has been nicknamed ‘Android Master Key.’ The vulnerability was originally discovered by the company Bluebox Security and I will let them take it away in explaining it to you:
The Bluebox Security research team – Bluebox Labs – recently discovered a vulnerability in Android’s security model that allows a hacker to modify APK code without breaking an application’s cryptographic signature, to turn any legitimate application into a malicious Trojan, completely unnoticed by the app store, the phone, or the end user. The implications are huge! This vulnerability, around at least since the release of Android 1.6 (codename: “Donut” ), could affect any Android phone released in the last 4 years – or nearly 900 million devices– and depending on the type of application, a hacker can exploit the vulnerability for anything from data theft to creation of a mobile botnet.
Not only has Saurik patched ‘Android Master Key’ and released it to the public for those that want to manually protect themselves though, he has also released a tool called Cydia Impactor that can root an Android phone or tablet utilizing the vulnerability. He has noted that it should “work up through approximately Android 4.1, including Glass and Google TV.”
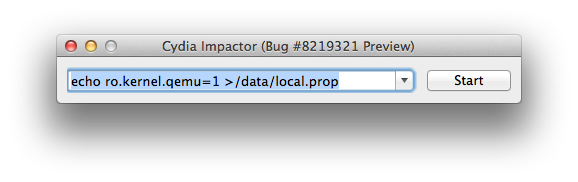
As 9To5Google explains “In true jailbreak fashion, the exploit [tool] runs from a Mac or PC and in a few steps gives your su/Root access to the infected phone/tablet. While it isn’t as plug and play easy as recent iOS jailbreaks, it is easy enough for anyone who wants to root their unpatched phone to do in a few minutes.”
Saurik plans to go into more detail on the vulnerability, his patch and Cydia Impactor next month at the annual Black Hat security conference in Las Vegas. In the mean time be sure to check out his in-depth article on the matter on his blog.
Thank you Saurik, your work is helping.
> Saurik plans to go into more detail on the vulnerability, his patch and Cydia Impactor next month at the annual Black Hat security conference in Las Vegas.
I am not giving a talk at either of these conferences, although I will be in attendance of both, and will likely be talking to a bunch of people about these very things in the hallway. The company that discovered the original Master Key exploit (without whose “hint” I may never have looked at any of this code at all) *is* giving a talk at Black Hat, which I mentioned a lot in my article; I am not exactly certain what he’s presenting.