By now if you have not heard of the Chronic-Dev Crash Reporter tool I would be surprised. Basically what this tool does is it stops your computer from sending crash reports present on your iPhone, iPod Touch and iPad to Apple when your sync your iDevice. It then uploads these crash reports to a private server that Chronic-Dev owns. The reason why Chronic-Dev wants your crash reports is because they think it will help find an vulnerability that can be worked into an untethered Jailbreak for the iOS 5 firmware generation.
Chronic-Dev released the Chronic-Dev Crash Reporter tool on November 27th, 2011, and today they have tweeted they have gotten about 10 million crash reports!
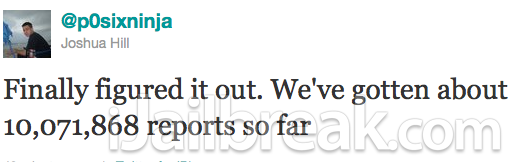
That is a phenomenal amount of crash report uploads in just about a week, and we can only imagine the amount of vulnerabilities that can come out of such an extensive database. Now one question I am sure is at the back of your mind is, how could one even go about going through 10 million crash reports? The answer is simple; Chronic-Dev plans to use a technology that was originally introduced by Google called MapReduce. What MapReduce allows you to do is rapidly process vast amounts of data in parallel on large clusters of compute nodes. P0sixninja notes that MapReduce should allow them to run tests that would take days normally in only seconds.
We will keep you updated on what comes from this massive database of crash reports. Until that time please stay tuned and leave any questions or thoughts in the comments section below…
Wow sounds like they are making progress.
sorry, but I know as a coder that maybe 2 of those are usable to exploits. Exploits are only formed from specific crashes, such as TIFF or GIF crashes and file crashes are not exploitable. Only those with buffer overflows, or bootrom can be exploited, and even that may not always be an exploit. There’s a difference between exploit and crash