Yesterday we told you about the worrisome SSL bug that affected both iOS and Mac. Of course Apple has already patched the bug, nicknamed Gotofail, on iOS but on the Mac the bug is still prevalent when using Safari. At first it was thought this bug only applied when users were browsing the net through Safari, but now it has been discovered the situation is much worse.
Private security researcher, Ashkan Soltani has found that the bug also affects other Mac applications such as Mail, FaceTime, Messages, Calendar etc., and not just Apple’s Safari browser. According to Forbes:
On Sunday, privacy researcher Ashkan Soltani posted a list of OSX applications on Twitter that he says he’s determined use Apple’s “secure transport” framework, the coding library that developers depend on to build programs that securely communicate online using the common encryption protocols TLS and SSL. The full list, which isn’t comprehensive given that Soltani only analyzed the programs on his own PC [..]
[..] The bug affects how Apple devices authenticate their secure connection with servers, allowing an eavedropper to fake that verification and hijack or corrupt traffic using what’s known as a “man-in-the-middle” attack. ”All these apps would be vulnerable to the same man-in-the-middle vulnerability outlined on Friday,” Soltani says.
It is worth noting that there is an extra layer of security in place for these applications, which may reduce the effects of the security vulnerability, but certain parts of the protocol like the initial handshake that rely on TLS could still be vulnerable to man-in-the-middle attacks. Furthermore, Apple’s update mechanism could also be vulnerable to spoofing.
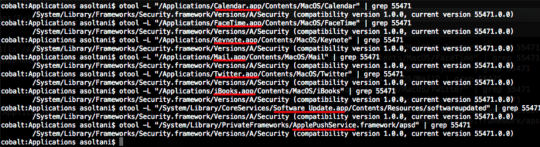
Red underlines show the vulnerable applications.
The vulnerability is a result of a silly error which some have even said was intentionally introduced by Apple, to give the NSA a way to tap into the data going through secure networks. So just what was this error? Well it emerged from the portion of the code that verified the authenticity of the server was never reached. Essentially someone on the same Wi-Fi network as you could intercept data and alter it / steal your sensitive information.
Right now your only protection from this vulnerability is to only connect to networks you trust, not public networks.
Leave a Reply